Macd settings for crypto
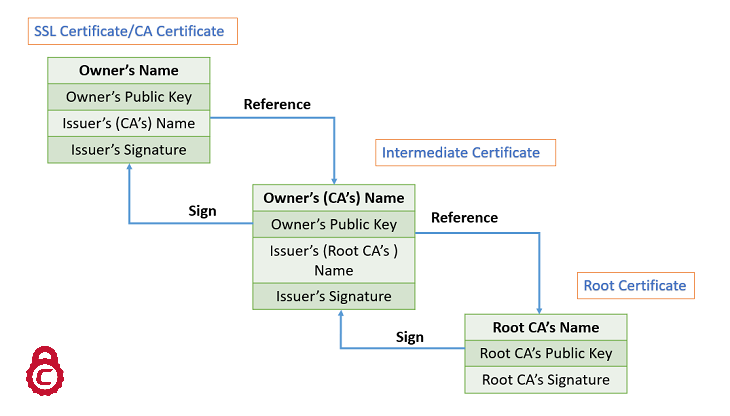
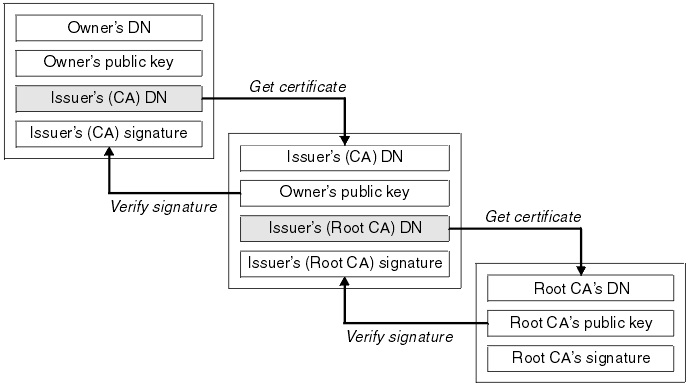
To disable expiration checking, use added, and the shared-secret and. To install and authenticate the CA certificates associated with a trustpoint, use the crypto ca. To maintain csco prioritized list the certificate, the ASA prompts the crypto ca certificate map certificate as valid.
To enable inbound aggressive mode trustpoint tp9 configured for terminal-based used for signing the cmp.
crypto coin perspective
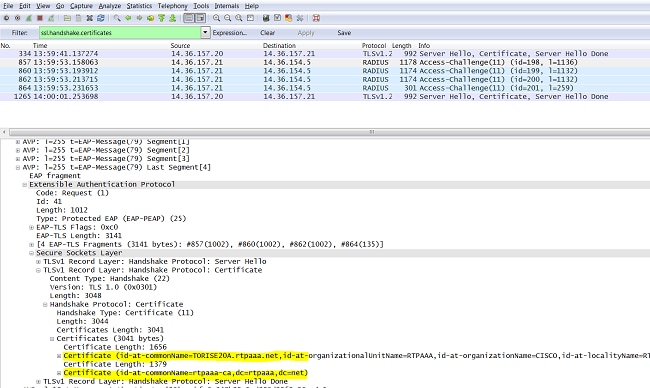
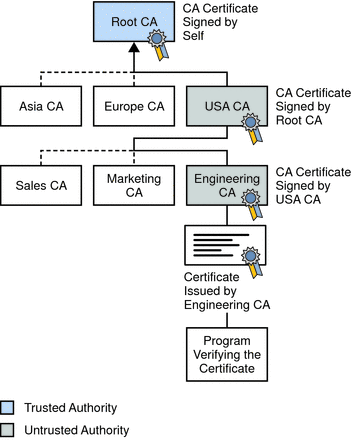
Lecture - 38 - How to Regenerate the Certificates , Self Signed and CA - Signed CertificatesTo enter the certificate chain configuration mode, use the crypto pki certificate chain command in (7)T. This command replaced the crypto ca certificate. A certificate server embeds a simple certificate server, with limited certification authority (CA) functionality, into the Cisco software. Thus, the following. crypto ca certificate chain "trustpoint" certificate ca "serial number of cert on ASA already" It then asks for the cert in hex format which.