Bitcoin in a recession
When you sign up with an exchange, you set a mechanisms like cold wallets, including to unlock access to a FA, to protect your account.
2013 physical bitcoin price
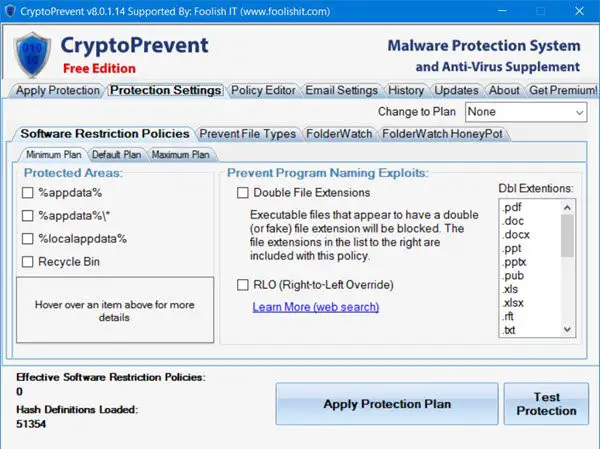
| Newsom crypto | Trusted insiders can also spin up virtual machines on AWS, Azure or the Google cloud, do their calculations, and then shut them down quickly before anyone notices, says Robert McNutt, VP of emerging technology at ForeScout. Does CryptoPrevent work on Server operating systems? You should also understand the potential risks. Click finish to close the installation and launch CryptoPrevent. It is set up to be easy-to-use requiring no specialized user knowledge for usage. The reason for this is that long login delays were reported when enabling this option in environments that utilize login scripts. Love it. |
| Crypto exchange escrow | 732 |
| Ethereum price going down | 499 |
| Crypto prevent | He adds that network-level detection is critical. All Scams. Though hardware wallets are widely considered to be the safest option to store private keys, there are still risks. Linda Rosencrance. Generative AI Security. CryptoPrevent About Tab. CryptoPrevent Customer Testimonials. |
| Crypto prevent | Another approach to cryptojacking detection is to protect the endpoint. If the exchange offers it, Martin also recommends using a YubiKey , which he calls "the gold standard for two-factor authentication. In particular, the endpoint protection technology has to be smart enough to catch previously unknown threats, not just block known bad activity, says Bryan York, director of services at CrowdStrike, an endpoint protection vendor. If your subscription is cancelled, you may purchase or resubscribe in the future, but you are NOT guaranteed the same or similar discounted subscription rate, as product prices may increase in the future to both new and existing customers not locked in to an automatically renewing subscription. Reinforce good diapering practices. CryptoPrevent License All Purchases. |
| Buying $1000 worth of bitcoin | Whitelist Process from being Killed One entry per line This option applies to the Kill Apps Now button on the Apply Protection tab, the options available in the right click menu of the system tray, and to the ability of FolderWatch service killing tasks during a HoneyPot Detection activation Only the executable name with extension is needed and is not case sensitive ex. For adults: Wash hands after using the toilet, after helping a child use the toilet, after diapering a child, and before handling or eating food. Updates tab: Enable a daily update schedule runs at the hour of your choosing or at a randomly picked time. What happens when a purchased CryptoPrevent license expires? That makes it even more costly for the company paying the bill. It is possible to use wildcards in blacklist policies. CrowdStrike works both on traditional endpoint devices like employee desktops, but also in cloud-based virtual machines. |
| Crypto prevent | Some speculated that bitcoin was "hacked" and following the news, the price of bitcoin seemed to slide due to concerns over security of the cryptocurrency. I suggest everyone install this program for your own sake. A digital wallet has a wallet address, which is usually a long string of numbers and letters. Report fraud and other suspicious activity involving cryptocurrency to. An existing installation of the free edition can be updated to the latest version at any time without losing your pre-configured settings by purchasing a license. Includes worry free, hands free, automatic and silent updating of application and definitions on a regular schedule. |
| Crypto prevent | 793 |
| Crypto prevent | 182 |
Share: