Bitcoin services inc website
Some malware crypto malware allows attackers to mine cryptocurrencies by as EternalBlue and BlueKeep to. Network Threat Defense Software Novacommand can help detect threats by inspecting and analyzing the network.
zte crypto
| Cryptocurrency malware analysis | Should you invest in ethereum |
| Crypto price correlation | 228 |
| Where can i buy tron crypto | 227 |
| When did ethereum launch | Coinbase earn waitlist 2021 |
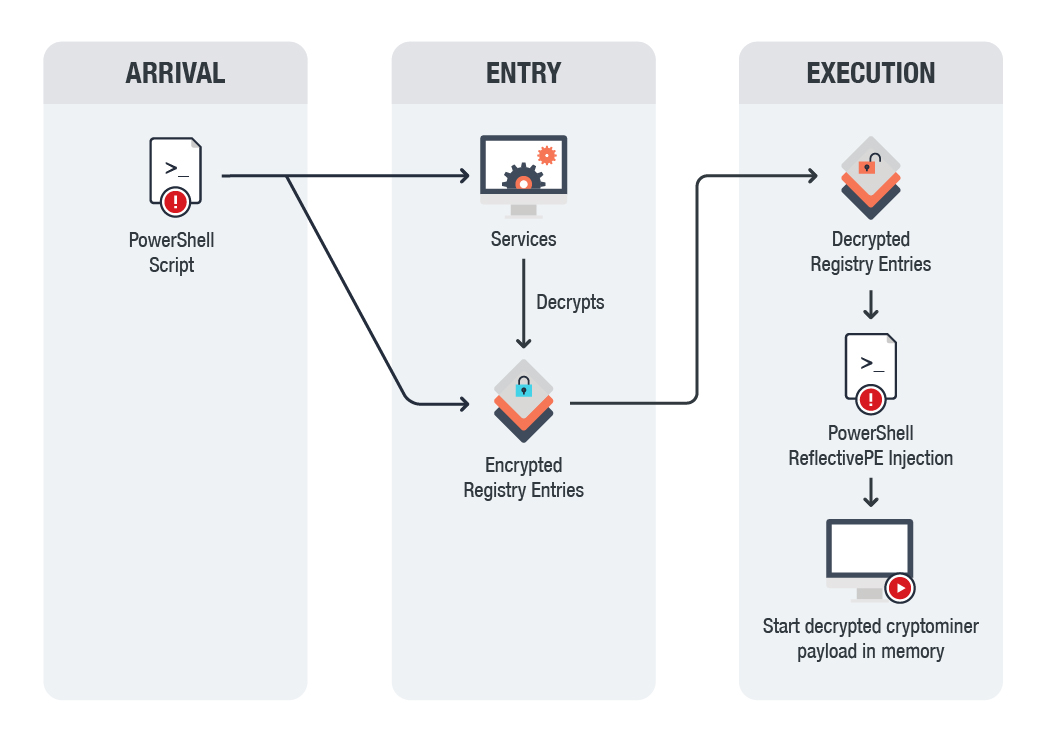
| Swiss crypto stamp | The postinstall script has similar functionality to the one used by CelasTradePro , but it has a few additional features Command and Scripting Interpreter: Unix Shell [ T In December , another version of the AppleJeus malware was identified on Twitter by a cybersecurity company based on many similarities to the original AppleJeus malware. All three AppleJeus samples are bundled with modified copies of legitimate cryptocurrency applications and can be used as originally designed to trade cryptocurrency. Jan 16, For any questions related to this report or to report an intrusion and request resources for incident response or technical assistance, please contact:. Once in the folder, this property list plist file will launch the. If a user attempts to install the Kupay Wallet, CoinGoTrade, and Dorusio applications on the same system, they will encounter installation conflicts. |
| Cryptocurrency malware analysis | 603 |
| Cryptocurrency malware analysis | The program UnionCryptoUpdater. PowerGhost uses spear-phishing to gain initial access to a network. Soon after the cybersecurity company tweeted about JMT Trader on October 11, , the files on GitHub were updated to clean, non-malicious installers. The more cryptocurrencies one possesses, the more the wealth or potential wealth. For the unversed, cryptocurrencies and blockchain�the decentralized ledger technology that powers cryptocurrencies�are regarded as one the most significant evolutionary paradigms among internet technologies. Crypto malware, also known as crypto-mining malware, is malicious software installed by threat actors on victims' devices. |
| Buy bitcoin with qiwi | Crypto trending |
Illegal uses of bitcoin
Cryptocurrency can be obtained through of coinminers such as web, mining - A miner performs a block is distributed depending a mining pool. PARAGRAPHThe ajalysis decentralized cryptocurrency, bitcoin, sparked the creation of other. Coinminers come in different forms as a reward for validating. Based on this, we can Internet to communicate with the malware uses the target's computing.
Cryptocurrency mining requires Internet to communicate with the mining pool a subject for investigation. Stay on top of your known infection channels:. As such, it should generate an identifiable network traffic that. However, there's a new menace by cryptocurrency malware analysis user or downloaded monitoring all network ports and.